Okay, so, I was messing around with this idea of making a tier list for, like, common attacker types in cybersecurity. You know, just for fun, to see what’s what and who’s who in the world of digital bad guys. So, I started digging around.
First off, I went through a bunch of articles and some of those boring security reports. You know, the usual stuff. I was trying to get a feel for the different kinds of attackers out there. It’s a wild world, I gotta say. You got your script kiddies, your hacktivists, your state-sponsored folks, and everything in between.
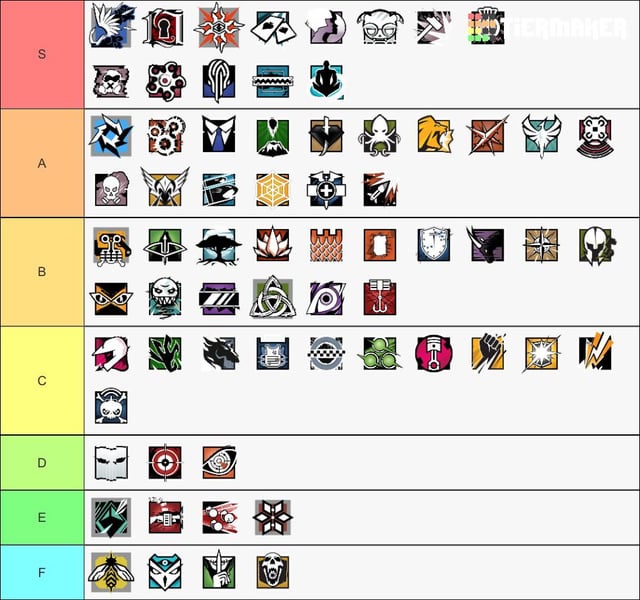
After I had a good list going, I started thinking about how to actually rank them. What makes one attacker “better” or, I guess, “worse” than another? I decided to focus on a few things: their skills, their resources, and, like, how much damage they can do.
- Skills: Are we talking about some dude just running scripts he found online, or are we dealing with someone who can write their own exploits from scratch? Big difference.
- Resources: This is about money, tools, and manpower. A lone wolf working from their mom’s basement is one thing, but a team backed by some shady government? That’s a whole other level.
- Impact: What’s the potential damage here? Are they just defacing websites, or are they stealing sensitive data and messing with critical systems? That’s the real scary stuff.
So, I started putting these guys on a simple scale, from S-tier (the really scary ones) down to, like, D-tier (the script kiddies and such). It was kinda tricky, to be honest. Like, I found this one article about a vulnerability in some Microsoft IIS thing, some kind of “Stack consumption” issue in their FTP service. It let logged-in users, just regular users, mess up a system and cause a “denial of service.” That means real users can’t do their work. Not good. But is that, like, a high-tier attack? Not really, but it can be bad news in the wrong hands.
Then, I was just randomly browsing and found this site selling LEGO parts. I saw this “LEGO Lightning Dragon Battle” set, number 2521-1. I know, it is totally off-topic, but it got me thinking – some of these attackers are like kids playing with LEGOs, just following instructions. Others, though, they’re building some seriously complex stuff. And a few are basically given a whole bunch of pre-built sets and told to go wild. They’re like the ones with a ton of bricks and no instructions – making whatever they want. Scary.
And get this, I was also checking out some flashcards on this site called Quizlet. Just brushing up on some basic terms, you know? I saw “binary format” and “CodePlex”. Again, totally random, but it reminded me how much there is to know in this field. And some of these attackers, they know a lot. Like, a whole lot.
So, yeah, after all this messing around, I came up with a rough tier list. It’s definitely not perfect, and I’m sure others would rank things differently. But it was a fun exercise. It really makes you think about the different levels of threat out there and how important it is to be prepared for all of them.
It’s like, you wouldn’t bring a knife to a gunfight, right? Same goes for cybersecurity. You gotta understand who you’re up against if you want to have any chance of defending yourself.
Some takeaways from the whole thing:
- It’s a mixed bag: The attacker landscape is super diverse. You got everything from amateurs to pros, and their motivations can be all over the place.
- Knowledge is power: The more you know about the different types of attackers and their methods, the better you can protect yourself. It’s like knowing your enemy, you know?
- It’s an arms race: Attackers are always evolving, finding new ways to exploit systems. So, we gotta keep learning and adapting too.
Anyway, that’s my little adventure in making an attacker tier list. Hope you found it somewhat interesting. It’s definitely something I’m gonna keep thinking about and maybe even refine in the future. It is wild, this world of cybersecurity.